
Filter Definitions
Setting up manual firewall filters

|
Filter DefinitionsSetting up manual firewall filters |

|
The Vigor routers allow you to set up specific IP packet filters whereby data packets are blocked or allowed through depending on criteria which you specify. The parameters you can select include IP address, port numbers, protocols and you can match ranges/subnets and chain many rules together to achieve complex filtering parameters.
Please note that to set up rules, you must be familiar with how IP address logic and subnet masks work. You can't damage the router by setting a bad filter, but you can stop any data flowing (albeit temporarily). Although the examples here might not match your particular requirements, we do recommend working through them here to gain a better understanding of how filtering works.
The Vigor router's can store up to 12 sets of 7 rules. Within each set, all seven rules are checked sequentially, unless the action of one rule forwards the packet immediately or triggers branching to another rule set. Each set does not automatically link onto the next set; a set must specifically link to another set if you want another set executed. If no rules within a set are matched then the packet is passed to its destination, unless the rule set is linked to another.
In this example, we want to block a PC with IP address 192.168.1.10 from browsing the web. They will still be allowed to use other Internet facilities such as email, FTP etc. Web browsing operates using TCP port 80. The rule can now be set up with the parameters we have :
Do remember that this rule will apply to the PC with that particular IP address. If you are using DHCP and do not otherwise fix IP addresses, the same PC might not always have that address. The Vigor's DHCP server can be set to always give the same PC the same IP address, or you can set it manually on each PC.
To enter our rule into the router, we select the Filtering/Firewall setup menu. Whilst in that menu, note that under the general setup options, we select the first rule set to execute. By default this points at rule set 2 for the data filter.
The router comes with a filter already set up for NetBIOS DNS lookups; that is rule no. 1 in set 2, so we can use rule no. 2 in that same set which, by default, is unused :
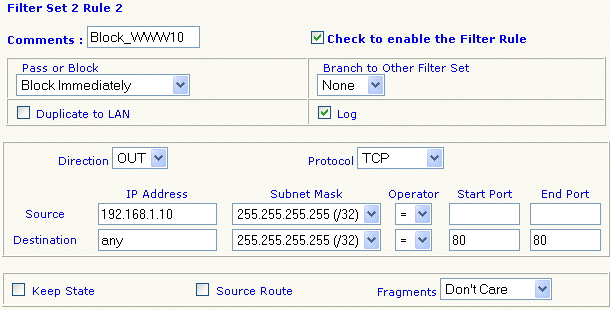
As shown, we give the rule a name to remind us what it's for, and then enter each of our parameters in the appropriate boxes. One optional feature we have selecting is the 'Log' checkbox. With this checked, any time the rule is matched, it will be logged; you can examine the filter log from the telnet prompt using log log -f command.
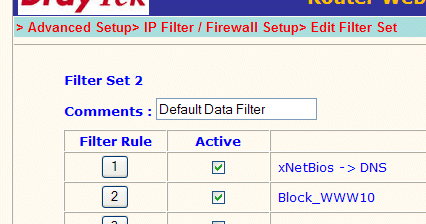
Once the above rule is saved, you can then test it. Go to the PC with the IP address 192.168.1.10, load up your web browser and try to access a web site. If the filter is working, the site will not appear (assuming that it worked fine before you set up the filter!).
In this example, we have several PCs, but we want to prevent internet access to all of them except the marketing department (two PCs), and our mail server. The mail server will only have access to outgoing mail protocols which are SMTP (TCP/25) and POP3 (TCP/110). We will need to have four rules for this :
| Rule 1 Allow Marketing PC1 | Rule 2 Allow Marketing PC2 | Rule 3 Allow mail server SMTP | Rule 4 Allow mail server POP3 Block everything else. |
|---|---|---|---|
|
|
|
|
|
Follow through the logic of the four rules above and you can see that we check each rule in turn, passing the packet immediately if we get a match. In the final rule, if the packet is NOT a POP3 packet from the mail server then the packet is droped (blocked). See how we have used the <> (not matched) comparison in the final rule, rather than the = comparison in the previous three.
NOTICE : This document is © SEG Communications and may not be distributed without specific written consent. Information and products subject to change at any time without notice.